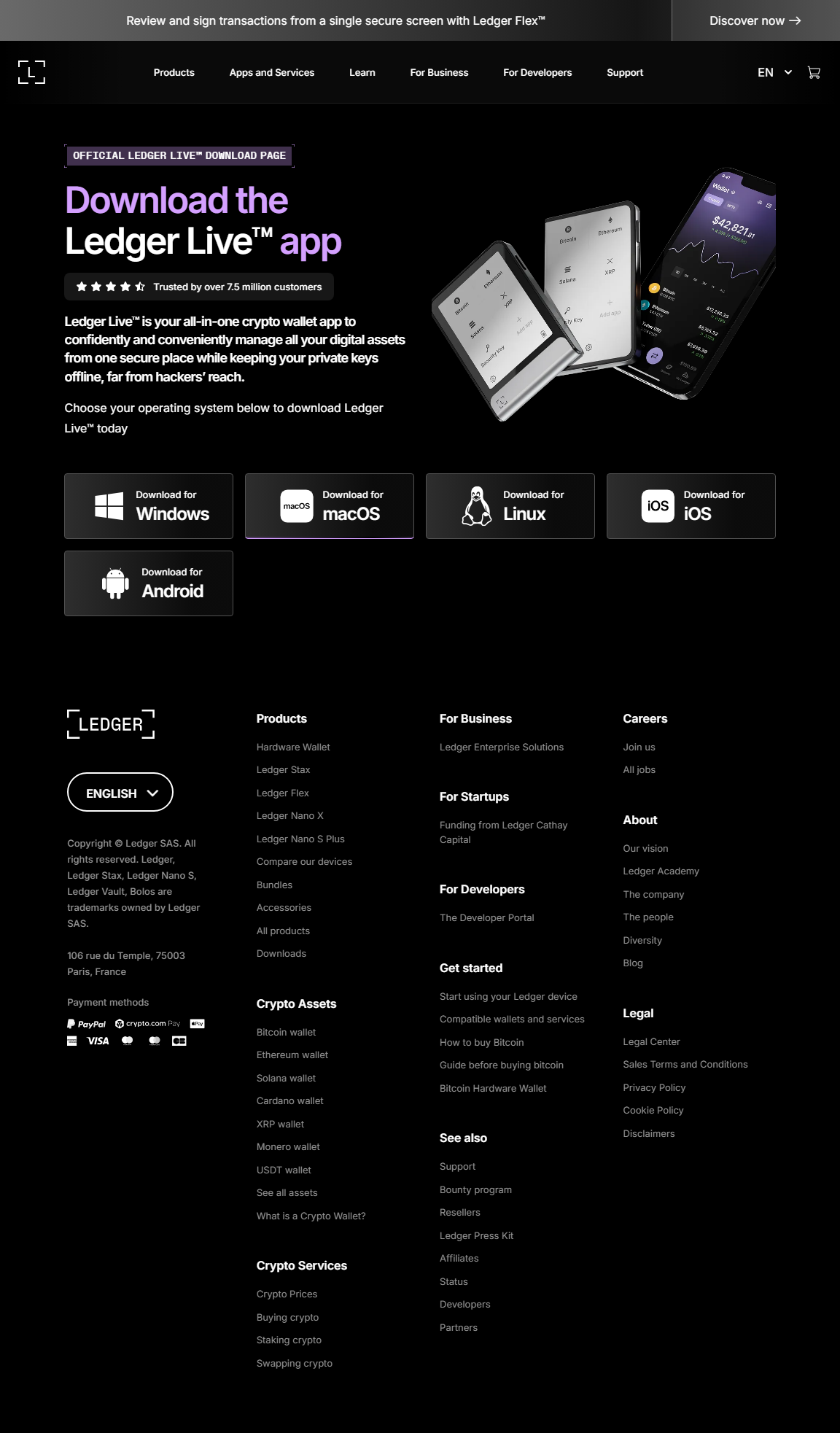
Ledger Login — Secure Access to Your Crypto Universe
Learn how Ledger Login safeguards your digital assets by providing a seamless, hardware-based authentication system that keeps hackers and phishing attacks at bay.
🔐 What is Ledger Login?
Ledger Login is the authentication method built into the Ledger ecosystem that allows users to access Ledger Live and other integrated platforms securely using their Ledger hardware wallet. Instead of entering passwords or recovery phrases, users verify their identity through cryptographic signing on their physical Ledger device — keeping private keys offline and invulnerable.
In essence, it transforms your Ledger device into a secure login token. No passwords. No cloud storage. Just your personal, tamper-proof device verifying access to your wallet every time you connect.
⚙️ How Ledger Login Works: Step-by-Step
1️⃣ Go to ledger.com/start
Start by visiting the official Ledger Start page. Download and install Ledger Live — the central app for managing your assets securely.
2️⃣ Set Up or Connect Your Device
Connect your Ledger Nano X, Nano S Plus, or Ledger Stax. Follow the on-screen prompts to set up or unlock your device with your PIN.
3️⃣ Open Ledger Live
Launch Ledger Live and select “Connect Ledger Device.” The software will detect your wallet and initiate the login request.
4️⃣ Confirm Login on Your Device
Check your device screen and confirm the login request. This physical verification step ensures your consent and protects against phishing or fake interfaces.
5️⃣ Access Your Ledger Live Dashboard
Once verified, you’re securely logged in. Manage your crypto portfolio, track performance, and transact directly — all from one interface.
🧠 Why Ledger Login Matters
Ledger Login solves one of crypto’s biggest challenges — security versus convenience. Traditional logins rely on passwords stored online, making them easy targets for hackers. Ledger’s model eliminates that risk by keeping private keys on a secure hardware chip.
- Offline Storage: Your private keys never touch the internet.
- Physical Confirmation: Every login and transaction must be approved on your device.
- Phishing-Proof: Device screens display authentic information, preventing malicious mimicry.
- Non-Custodial Control: You remain the only one who can access your assets.
📊 Ledger Login vs. Traditional Logins
| Feature | Ledger Login | Password Login |
|---|---|---|
| Security Level | Hardware-level encryption | Vulnerable to hacks |
| Authentication Method | Device confirmation | Text-based password |
| Data Storage | Offline (inside device) | Online or cloud databases |
| Ownership | Full user control | Controlled by third-party servers |
| Phishing Protection | High (device screen verification) | Low (fake sites may mimic login) |
💬 Common Questions About Ledger Login
1. Can I use Ledger Login without the device?
No. You must physically connect or pair your Ledger hardware wallet to complete login verification.
2. What happens if my Ledger device is lost?
Your crypto remains safe. You can restore access using your 24-word recovery phrase on a new device.
3. Is Ledger Login compatible with mobile devices?
Yes, Ledger Live Mobile supports Bluetooth login for Ledger Nano X and Ledger Stax.
4. Is it possible to access Ledger Live without logging in?
You can use watch-only mode to view your portfolio, but transactions require authentication via Ledger Login.
🚀 Start Your Secure Journey with Ledger Login
Ledger Login represents the future of crypto security — passwordless, decentralized, and built entirely around user sovereignty. It’s more than just access — it’s digital freedom in your hands.
Get started safely through the official setup path: ledger.com/start.
© 2025 Ledger Login Guide. All Rights Reserved. | Built for crypto enthusiasts and investors.